GCP Privileged Access Management: The Key to Effective Privilege Management
Privileged Access Manager (PAM) is a powerful tool for managing and controlling access to sensitive systems and data. One of its key features is the ability to provide just-in-time (JIT) privilege elevation, allowing users to temporarily access elevated privileges only when necessary.
How PAM Works:
- Create Entitlements: Define the specific privileges or roles that can be granted and who is authorized to request them.
- Request Privileges: When a user needs elevated privileges, they submit a request.
- Approval Process: Depending on the entitlement, the request may require approval from designated approvers.
- Grant Privileges: If approved, the user is granted the requested privileges for a specified duration.
- Revoke Privileges: The elevated privileges are automatically revoked once the designated time period expires.
USE CASES:
- Sensitive Resource Control: Restrict access to sensitive data and systems, requiring approvals and justifications.
- Emergency Access: Quickly grant privileges to authorized personnel during critical situations.
- Development and Support: Grant temporary privileges to developers and support engineers for specific tasks.
- Service Account Management: Secure service accounts by allowing them to elevate privileges only when necessary.
- Contractor and Extended Workforce Access: Manage access for external users, ensuring proper approvals and justifications.
Supported Resources and Roles:
- Entitlements: Can be created for projects, folders, and organizations.
- IAM Conditions: Can be added to limit access to specific resources within an entitlement.
- Roles: Supports predefined and custom roles, but not basic roles.
Identity Support:
- Various Identity Types: Supports Cloud Identity, Workforce Identity Federation, and Workload Identity Federation.
Audit Logging:
- Detailed Logs: Tracks events like entitlement creation, grant requests, and reviews.
- Log Retention: Grants are kept in Cloud Audit Logs for 30 days.
Grant Retention:
- Automatic Deletion: Grants are automatically deleted after 30 days of being denied, revoked, or expiring.
PRE-REQUISITES:
To effectively work with entitlements and grants in Privileged Access Manager, ensure you have the necessary permissions. Request your administrator to grant you the following IAM roles at the organization, folder, or project level:
For creating, updating, and deleting entitlements:
- Privileged Access Manager Admin (roles/privilegedaccessmanager.admin)
Additionally, one of the following:
- Folder IAM Admin (roles/resourcemanager.folderIamAdmin)
- Project IAM Admin (roles/resourcemanager.projectIamAdmin)
- Security Admin (roles/iam.securityAdmin)
For viewing entitlements and grants:
- Privileged Access Manager Viewer (roles/privilegedaccessmanager.viewer)
For viewing audit logs:
- Logs Viewer (roles/logs.viewer)
BRIEF STEPS TO CREATE ENTITLEMENT:
In the context of Privileged Access Management (PAM), an entitlement is a defined set of privileges or permissions that can be temporarily granted to authorized users. It acts as a template for granting specific roles or access rights for a limited time.
Here’s a breakdown of what an entitlement typically includes:
- Roles: A list of specific roles or privileges that can be granted.
- Requesters: The individuals or groups who are authorized to request these privileges.
- Approvers: The individuals or groups who can approve or deny grant requests.
- Conditions: Any conditions or criteria that must be met before a grant can be approved.
- Duration: The length of time for which the grant will be active.
In order to create entitlements, first one needs to set up the PAM. PAM can be set up at any level of resource. The procedure to set up PAM is as shown below:
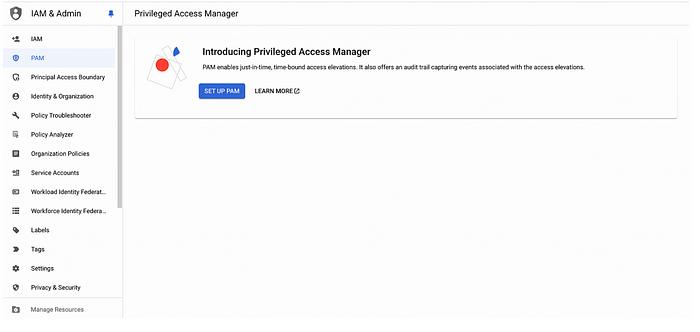

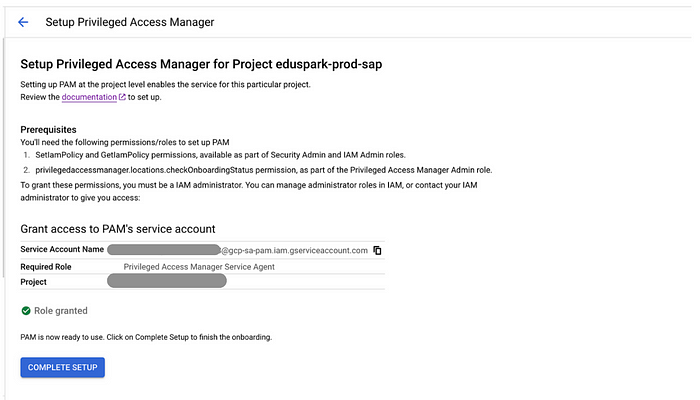

PAM setup is complete. Now, we can proceed to create Entitlements as shown below:
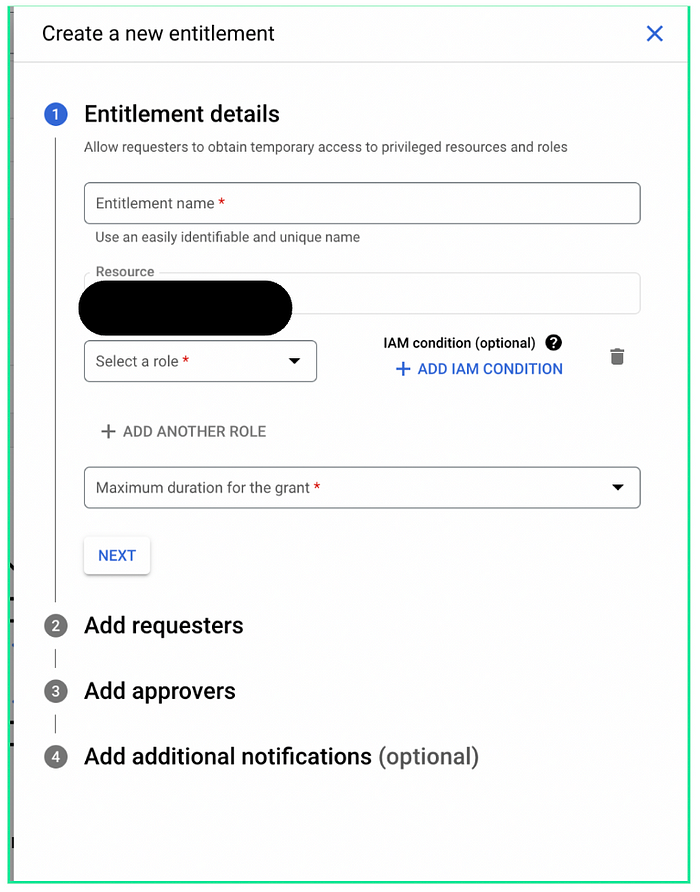


allUsers and allAuthenticatedUsers. You can add more than 20 identities by adding them to a group and listing the group in the entitlement.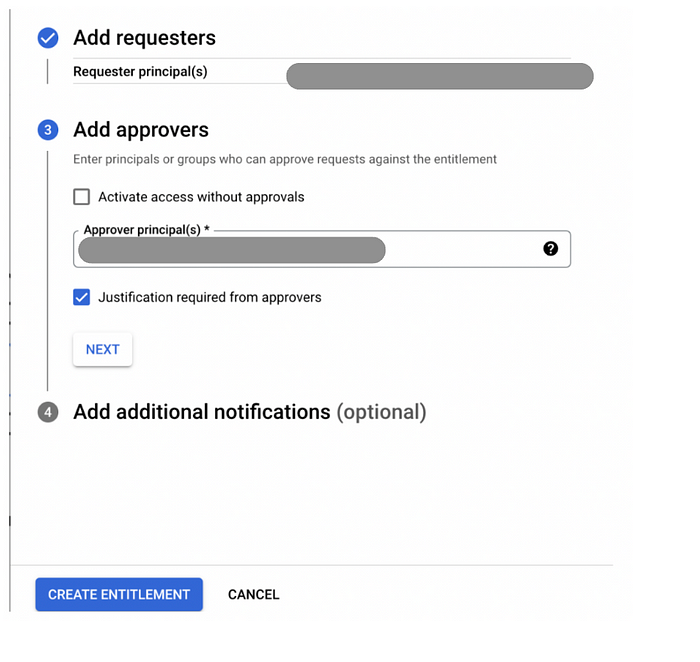

Scope and Hierarchy:
- Organizational Level: Entitlements created at the organization level apply to all folders and projects within that organization.
- Folder Level: Entitlements created at the folder level apply to all projects within that folder.
- Project Level: Entitlements created at the project level apply only to that specific project.
Limitations and Considerations:
- IAM Policy Modifications: Manual modifications or Terraform authoritative resources can interfere with PAM’s functionality.
- Avoid including roles that allow users to modify their own permissions. These roles, like those with
setIamPolicyoriam.roles.updatepermissions, can be used to escalate privileges. Instead, use roles that grant only the necessary permissions for the task at hand.
CONCLUSION:
In conclusion, PAM is a powerful tool for managing privileged access. It helps organizations:
- Reduce risks: By limiting access to elevated privileges.
- Improve compliance: By tracking and auditing privileged activity.
- Increase efficiency: By streamlining the process of requesting and granting privileges.
To get the most out of PAM, it’s important to:
- Understand its capabilities: Know what PAM can do.
- Create effective entitlements: Define the roles, requesters, and conditions.
- Follow best practices: Avoid using roles that can be used to escalate privileges.
By following these guidelines, organizations can effectively use PAM to enhance security and control privileged access.
REFERENCES:
- PAM Overview: https://cloud.google.com/iam/docs/pam-overview
- Enabling PAM — https://cloud.google.com/iam/docs/pam-permissions-and-setup
- Creating Entitlements — https://cloud.google.com/iam/docs/pam-create-entitlements
